7 Cybersecurity Threats to be Aware of in 2023
Cybersecurity is not a novel term to which you need an introduction. Every year a new set of threats emerge to challenge us. Only to make us better prepared. Cybersecurity is one of those persistent threats that returns every year. In the first half of 2022, there were 2.8 billion malware attacks worldwide. Only the first half! Cybersecurity threats are indeed bigger in scheme and plot. This is why we bring you the threats to be aware of in 2023.
But before we begin the list of threats. Here are the ideas we will touch upon in the following blog.
Why does cybersecurity need your attention?
IT security investment is a significant portion of the digital transformation wagon we all are sitting over. Last year, spending on digital transformation technology was 1.8 trillion dollars! But how much of it was used for security infrastructure?
In India, 68% of companies have experienced some form of data breaches since the pandemic. Where 7 out of 10 Indian companies experienced a ransomware attack just last year.


These numbers come in the wake of rising new technologies. That may be connecting us on the global front in business but also welcoming new types of cybercriminals and cyber attacks. 65% of executives believe these attacks will only increase in 2023. So what is the action plan from here? Are we as prepared as we should be? There is no concrete answer to this. But to formulate a better response, gaining an idea of looming cybersecurity threats is a must.
Because the damage of a threat is unfathomable. It can either completely impair a business or lead to difficult-to-recover losses.
What are the threats you need to look for?
We have so far seen the impact of this threat. And the terror it possesses for the IT market. By 2025%, almost 60% of companies plan to do a risk analysis before doing a 3rd party transaction or business engagement.


Massive, isn’t it? So without further ado, let’s now look at the cybersecurity threats for 2023.
IoT and Web3
IoT, or the Internet of Things, expands the internet-connected landscape, thus becoming more vulnerable to attacks. Communication between multiple devices opens IoT to unknown software bugs and attacks. The reason is often simple-to-guess credentials and default passwords.
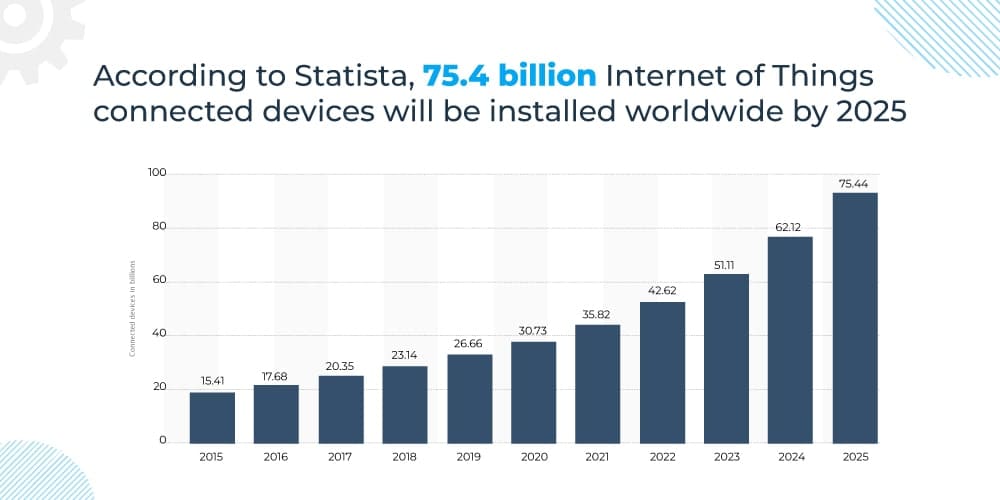

Moreover, the use of IoT is only rising (it was 60% in 2020). With the influx of a global lockdown, remote and hybrid means are here to grow. So being cautious right from the moment of installation is fundamental.
Web3 is a reasonably new player in the industry. That aims to decentralize power from the bigger companies among users via:
- Cryptocurrency
- Token-based economics
- And blockchain.
As enticing as a new avenue looks, it is not free of risks and threats. Rush in implementation often leaves loopholes and unaddressed flaws. But this is preventable. A basic check and you save loads of sensitive data.
Crypto
We briefly touched upon the word. And I am sure many of you are already investing in this not so novel anymore scheme. But attacks via crypto are a serious threat today. A part of the web3, you will be surprised to know that in 2021, 60% of trojan activity was by crypto miners!
The impact may not be on your physical devices but your monetary bills. The prices may inflate with no idea of where it is all going.
So yes, a novelty in technology also means originality in cyber threat.
Cloud Security
Put that on the cloud! Our most convenient tech aid today is the cloud. Because it is easy to maintain. There is a common notion that the cloud is very secure. It is but not entirely. Of course, it has the edge over on-premise systems, but something can go wrong. And that ranges from,
- Misconfigured cloud settings due to a lack of proper cloud setup.
- Data loss due to irregular backups and further exposure to ransomware.


- API (Application Programming Interfaces) vulnerabilities due to the APIs being insecure (a lot of times).
- Malware infections entrance is as easy as handling the cloud. Once in, it can loot your data.
- Insufficient identity and access management controls in companies after cloud migration.
All these are gaps. That need to be closed when you work with the cloud. Because the potential looters are prying to gain access. So look closely.
Staffing Issue
The lack of a properly well-trained, well-equipped IT staff can cause tremendous pressure on the organization’s IT needs. To make matters worse, a considerable skill gap is associated with a lack of staff, layoffs, and pay cuts.
And the staffing gap is increasing year after year. The standing security workforce is at 4.7 million. Further, needing an additional 3.4 million to undertake cyber security properly.


Moreover, an overburdened IT staff is bound to exhaust in fulfilling the needs. And lead to further exposure to cybersecurity threats.
Phishing attacks
After 2020, phishing attacks have become more mature and sophisticated. So much so it is an industry in itself. Last year a total of 3394662 attacks happened in the first 3 quarters! And the prediction for 2023 says that the trend will continue. Because more people are turning to cybercrime for financial gain. More so in a time where economic vulnerability is faced by everyone with varying intensity. A high vulnerability is expected for e-commerce sites as they are prone to transaction-related attacks. Thanks to the growing online shopping community.


Moreover, In February last year, around 1.7 million NFTS were stolen via a phishing attack on OpenSea users, according to Forbes.
This only implies phishing attacks are a major part of the world’s growing technological development. Contributing to the world’s greatest resource downfall.
AI
AI or Artificial intelligence is one of the technological fronts rapidly getting infused into our day-to-day functioning. Out of which, consumer and enterprise AI use is bound to grow in 2023.
Although AI adds to the security front, privacy and security here can be a cause of concern. Even while it is helping with building automated security systems, face detection, automatic threat detection, and natural language processing. Actions like:
- Malware run on AI
- AI-enabled attacks like deepfakes ( digital alteration of appearance) under social engineering attacks
- Harm AI models with inaccurate data
- AI-powered malware (where Machine Learning is trained to think for itself)
- Map legitimate AI for improving their attack
Can defeat the purpose of AI.
Automation
Increasing data demands and even more voluminous data storage is pushing professionals to seek automation. Besides hectic work, the promise of quick and efficient solutions leads them towards AI.
But the size is what can become a reason for the automation threat. Often large/ complex web applications pave the way for insecure automation because of the difficulty in application.
In addition, attackers are now using automation by overpowering them and conducting more sophisticated attacks than ever. So the pros and cons of automation have to be well analyzed in mitigating cyber attacks.
In conclusion
The amount of cybersecurity threats we see today is turning clever. With the advent of better and able technologies, threats are also rising. And every year, this face of threats changes too.
But down the line, a fundamental lack of security puts us off. This can be avoided. Just like we hurry to try all that novelty, assured safety needs that attention too.
With the above pointers, we aimed to draw attention to how threats can become overpowering if not controlled at the beginning. Suppose you got any suggestions or queries for us. Please feel free to drop them in the comments or connect with us for the same.