Business Identity Theft: Protecting your brand’s Integrity
You design your brand with all heart and soul. But some hostile actor comes in and attacks you with business identity theft. More than the damage it does to your morale, it hits your business in all the wrong ways. According to LexisNexis, the average number of frauds increased from 43% to 48% for mid-to-large retailers and 27% for small businesses (as per their 2020 data).


Impersonating or pretending to be you is a common evil practice across the industry. Giants like Microsoft and Google face it the most. But do have acts up their sleeves to protect and act. In our discussion today, we also extend our thoughts on the idea of business identity theft. And how you can safeguard your online business by knowing the nitty-gritty of this malpractice.
- Business Identity Theft: Meaning
- Who gets impersonated
- Ways of Impersonation
- Signs to look for
- Types of Impersonation
- How identity theft is done
- Steps to protect from identity theft
What is meant by business identity theft?
It is a type of cyber attack scam where someone poses as you. The practice of brand theft is a much more sophisticated form of phishing. Because your identity, reputation, and name are used to commit fraud across your customers.’
- Hard-earned money,
- Sensitive data,
- Login IDs and passwords.
Where the message is sent out as a trap to capture your customers or potential buyers. The fraudster makes them believe that it’s your store or brand. And the customer then sends in information thinking it’s you.
Business Identity Theft works because the scammers use your created value for their gains. They use a mass approach that works when only some among the masses fall for it. Common practices include:
- Logging in to steal your customer’s IDs and passwords
- Making sums of payments to their accounts


- Installing malware to steal and fetch your customer’s data
They often involve an urgency in the tone. Brand impersonation hotspots begin with emails, text messages, and calls. (More of which we will be discussing).
Here’s an example to highlight the scale of brand impersonation.
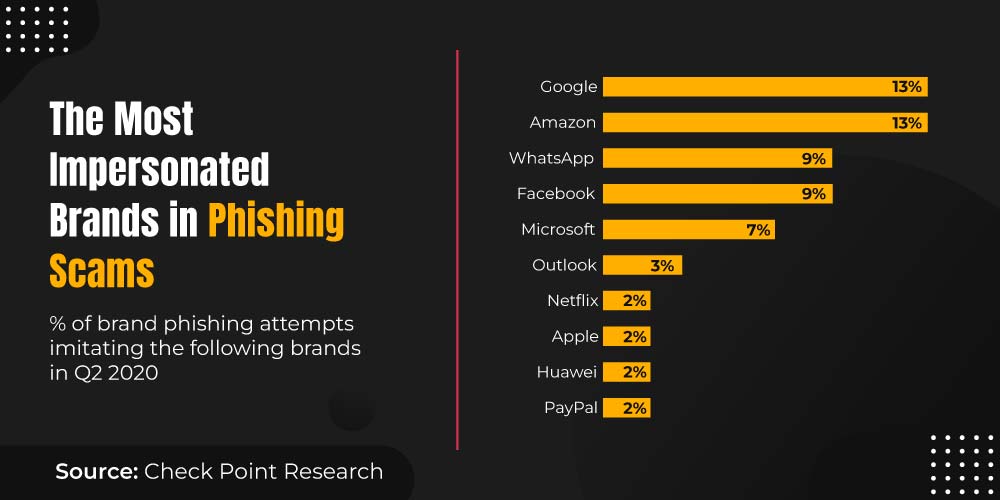

Who gets impersonated using your brand name?
Learning about the probable agents from your organisation or brand that get impersonated to attract your customers is essential. Mostly, the agents with high authority positions are the target sets whose identity is used to fake in front of your customers.
That is,
- Your CEO or senior executive to steal sensitive organizational information from junior employees.
- Your brand name in an email spoof.
- Your third-party vendor (say your payments/ checkout partner)
Ways of impersonation
On the pretext of the mentioned agents, these fraudsters get into your partners and customers via the following ways.
Have you heard of malvertising?
So is this what we found during our study. Some Amazon sellers used the Amazon root domain to attract customers to their products instead of the actual site. When you browse on a search engine, and instead of Amazon’s main page, you land up on a particular product, you know now what has been done.
But this is just one way of what gets done. Standard practices or methods today include:
Creation of Fake social media accounts
A recent example is when Twitter gave away verified handles after the pay to non-authentic individuals. Apart from this, many malevolent actors use your brand name and create fake accounts impersonating you to lure you with their schemes.
Fake mobile applications
It is not uncommon if imitating your website is something they can do. Creating a fake mobile application is relatively easy too. This gets riskier as it gets direct access to all your phone data and exploits them without your customer’s knowledge. The game is challenging. But as a brand, you must report and check for applications that act like you.
Faking your website with lookalikes
We mentioned the practice of malvertising. But that’s not all. Fraudulent agents also fake your websites to steal from your customers. The difference may be subtle, but it’s essential to identify if the same is real or fake.
Taking over your executive’s accounts
To make it look like them, taking over executive accounts is common to sound trusted in an official mail address.
Email spoofs
These are the most common. The actors often tweak a character or brand name in a fashion that consensus your audience and make them fall for their message.


Therefore, check out these signs to be wary of them.
Signs to Look for
- Asking you to keep the exchange private and very confidential. And these words have repeat highlights in the mail.
- Urgency and pressure to act as soon as possible on their shared directive.
- Language, grammar and spelling are out of place and not authentic.
- Receiving an unusual mail or message that is not coming from the process you are familiar with.
- Wrong email addresses (although difficult to identify if the legitimate source gets taken over)


Types of impersonations
Impersonationating actors who loot your business identity come forward and plan the following types.
- Fake malware alert that prompts tech protection installments on your customers’ devices.
- Subscription emails that ask customers to get refunds for their discounted purchases.
- Recruitment scams pose an authoritative company to scam people of money.
- Undertaking vishing (voice phishing), that is, they call up posing as your brand to steal customers’ valuable data. Make them believe that you are offering and doing what they do with emails instead.
How identity theft is done
The attackers move with a strategic plan to build up your identity. They first begin with:
Organising and listing the targets to approach
This means the attackers look for brands with high-value assets or underdeveloped IT infrastructure. Because that will dictate their actions against your brand.
Once they locate your brand, they look for the target audience you cater to win over them.
Prepare the fake assets
Once your brand comes under the attackers’ radar. Next is cloning your website/ apps/ executive handles or the social media handles that you use. All done to look like you, show like you but act like they want.
Attacking your customers
Once the above steps are through. The malicious actor then uses all the communication channels to sabotage your credibility.
Steps to protect from impersonation
Business identity theft is not undefeatable. If you take the right call, these then become resolvable. All you need is planning and foresight to avoid losing revenue and value. Let’s see how.
- Protect your domain name. By
- Renewing domain names by keeping an internal tab.
- Keep checking abandoned domain names and renewing them if possible to avoid attackers taking over your residue traffic.
- Make yourself aware of cyber attacks, as awareness is the most important key here.
- Limit your registrar account and DNS settings access to reduce the vulnerability of your site’s access.
- Secure the domain with SSL/ TVS/ EV certificates.
- Register your logos, trademarks, and product images. Keep a tab on trademarks, as your loss can lead to the attackers’ gain.
- Work on creating a brand identity and voice that’s uniform all over. Because that way, automated checking can help you find impersonated images and logos.
- Gain access and control over social media platforms. That is, be present across all major social media platforms to avoid having your copies there.
- Teach your employees and make them aware of business identity theft. Show the hows and whats and signs to look for.
- Build a good rapport and link with law enforcement agencies. To ensure better handling of your revenue losses and catching the culprits.
- Work on a team of incident responders to highlight the sprouting issues. All done to minimise the actual damage.
- Make sure to use verified mark certificates and brand indicators of message identification in your emails to customers. To establish more authority over your brand.
- Send warning emails and messages to your customers to develop well-being and value. And be wary of fraud.
- Digitally sign your emails to preserve your integrity.
- Set up Google Alerts to monitor the use of your brand name online.
- Safeguard your secrets at all costs.
In conclusion
This discussion on the malpractice of business identity theft sums up for now. But the scope and possibilities of expansion are always present. And we look forward to your contributions to this discussion as identity theft perils take more than your brand builds in years.
So connect with us if you got something important. We look forward to the interaction. If not, do tell us about your thoughts on business identity theft. Till then, keep reading.